Enable Logging to Your Own S3 Bucket
Prerequisites
Full administrative access to the Cisco Muti-org console
A login to AWS Management Console. If you don't have an account, Amazon provides free sign up for S3.
Note: Amazon requires a credit card in case your usage exceeds free plan usage.A bucket configured in Amazon S3 to be used for storing logs. For more information, see Set up an Amazon S3 Bucket and Amazon S3 documentation.
Enable Logging
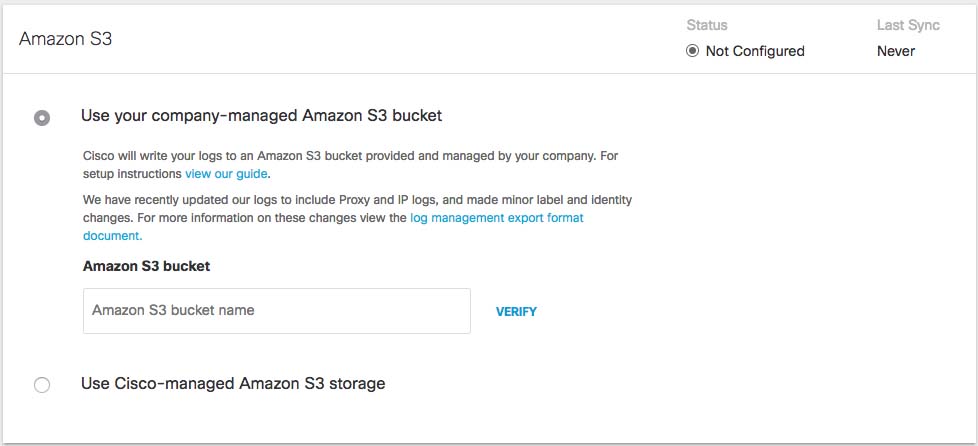
Navigate to Console Settings > Log Management and select Use your company-managed Amazon S3 bucket.
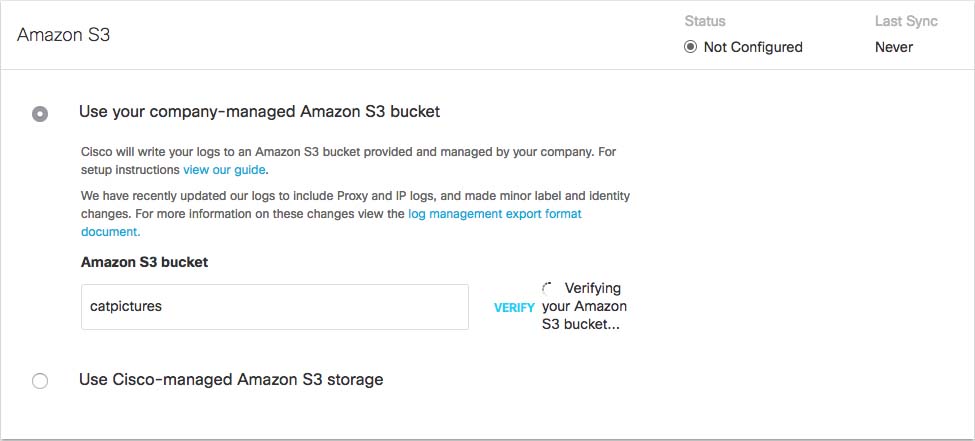
In the Bucket Name field, type or paste the exact bucket name you created in Amazon S3 and click Verify.
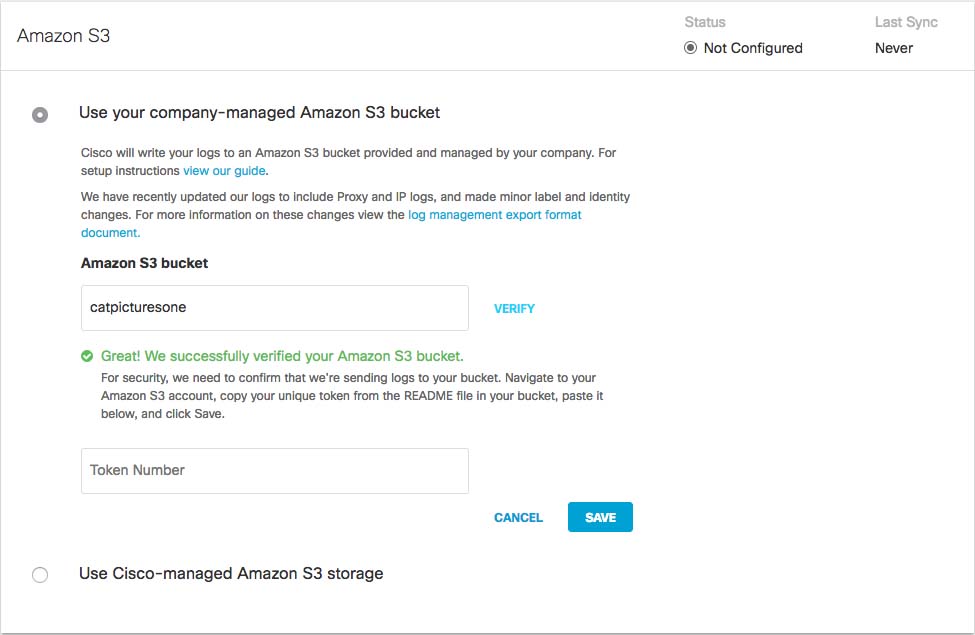
Umbrella verifies your bucket, connects to it, and saves a README_FROM_UMBRELLA.txt file to your bucket.
Open the README_FROM_UMBRELLA.txt file Umbrella saved to your bucket, copy and paste the token listed in it into Token Number, and click Save.
Manage Logs < Enable Logging to Your Own S3 Bucket > Set up an Amazon S3 Bucket
Set up an Amazon S3 Bucket
Before you can configure the Multi-or console to store your organization's logs to your own self-managed Amazon S3 bucket, you must first set up an Amazon S3 bucket. For information about how to do this, see Amazon's S3 documentation.
JSON Bucket Policy
When setting up your bucket, you are required to add a bucket policy so that your bucket can accept uploads from your organizations' Umbrella dashboards. Copy and paste the following JSON string, which contains the preconfigured Umbrella bucket policy, into your Amazon S3 policy.
{
"Version": "2008-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568526795995:user/logs"
},
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::bucketname/*"
},
{
"Sid": "",
"Effect": "Deny",
"Principal": {
"AWS": "arn:aws:iam::568526795995:user/logs"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::bucketname/*"
},
{
"Sid": "",
"Effect": "Allow",
"Principal":
{ "AWS": "arn:aws:iam::568526795995:user/logs" }
,
"Action": "s3:GetBucketLocation",
"Resource": "arn:aws:s3:::bucketname"
},
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568526795995:user/logs"
},
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::bucketname"
}
]
}
Enable Logging to Your Own S3 Bucket < Set up an Amazon S3 Bucket > Enable Logging to a Cisco-managed S3 Bucket
Reference Link : https://docs.umbrella.com/deployment-umbrella/docs/manage-logs